nuclei - 基于简单 YAML 的 DSL 的快速且可定制的漏洞扫描器
基于基于YAML的简单DSL的快速且可定制的漏洞扫描程序。
如何 • 安装 • 对于安全工程师 • 对于开发人员 • 文档 • 制作人员名单 • 常见问题解答 • 加入不和谐
Nuclei 用于基于模板跨目标发送请求,从而实现零误报,并在大量主机上提供快速扫描。Nuclei提供各种协议的扫描,包括TCP,DNS,HTTP,SSL,File,Whois,Websocket,Headless等。借助强大而灵活的模板,Nuclei可用于对各种安全检查进行建模。
我们有一个专用的存储库,其中包含由300多名安全研究人员和工程师提供的各种类型的漏洞模板。
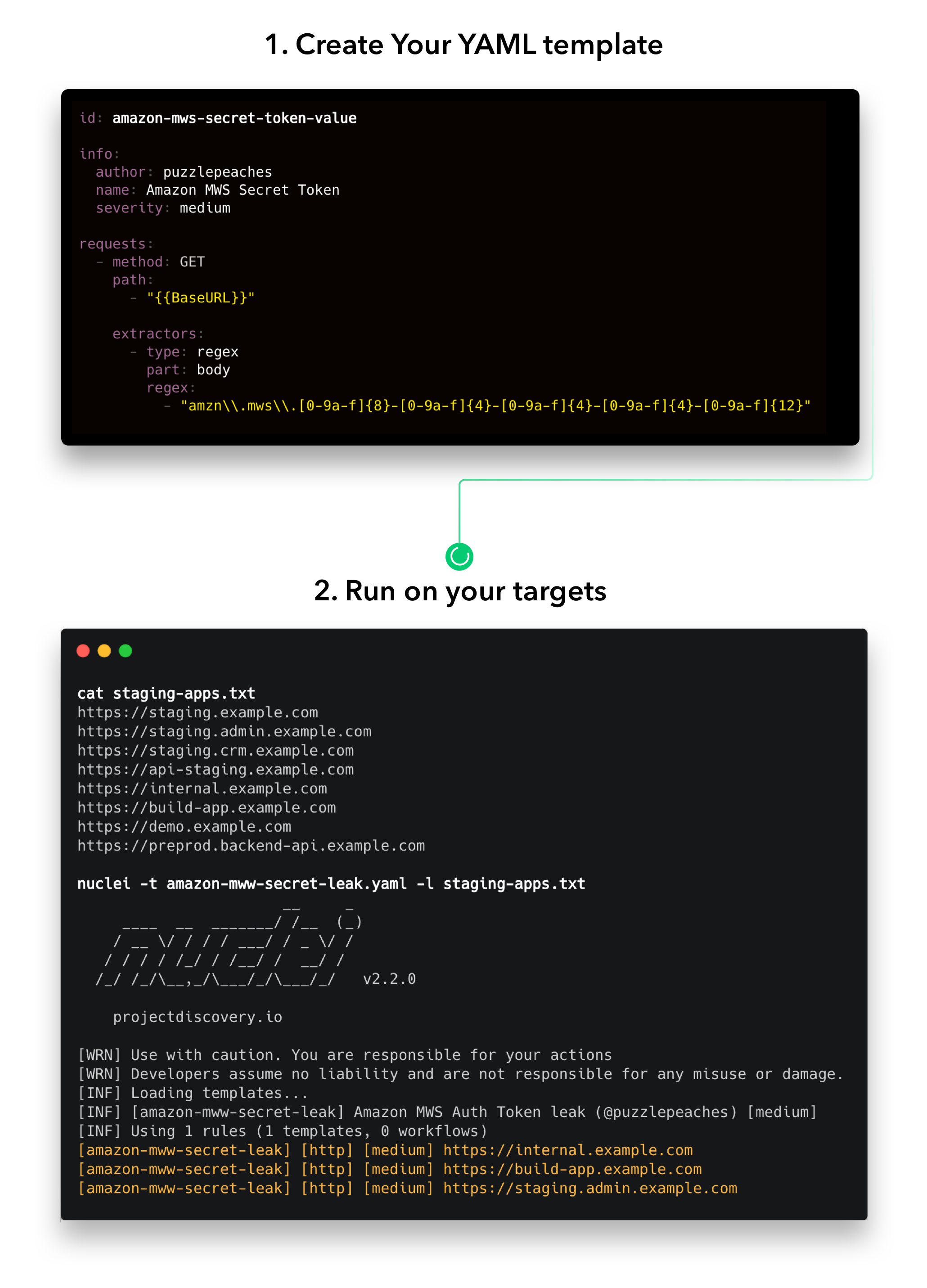
它是如何运作的
安装原子核
Nuclei 需要 go1.17 才能成功安装。运行以下命令以安装最新版本 -
go install -v github.com/projectdiscovery/nuclei/v2/cmd/nuclei@latest可以在此处找到更多安装方法。
原子核模板自版本v2.5.2起,Nuclei默认内置了对自动模板下载/更新的支持。Nuclei-Templates项目提供了一个由社区贡献的即用型模板列表,该列表会不断更新。 你仍然可以随时使用该标志来更新核模板;你可以为个人工作流程编写自己的检查,并需要遵循Nuclei的模板指南。 update-templates YAML DSL 引用语法可在此处找到。 |
用法
nuclei -h这将显示该工具的帮助。以下是它支持的所有开关。
Nuclei is a fast, template based vulnerability scanner focusing
on extensive configurability, massive extensibility and ease of use.
Usage:
nuclei [flags]
Flags:
TARGET:
-u, -target string[] target URLs/hosts to scan
-l, -list string path to file containing a list of target URLs/hosts to scan (one per line)
-resume string Resume scan using resume.cfg (clustering will be disabled)
TEMPLATES:
-nt, -new-templates run only new templates added in latest nuclei-templates release
-ntv, -new-templates-version string[] run new templates added in specific version
-as, -automatic-scan automatic web scan using wappalyzer technology detection to tags mapping
-t, -templates string[] list of template or template directory to run (comma-separated, file)
-tu, -template-url string[] list of template urls to run (comma-separated, file)
-w, -workflows string[] list of workflow or workflow directory to run (comma-separated, file)
-wu, -workflow-url string[] list of workflow urls to run (comma-separated, file)
-validate validate the passed templates to nuclei
-nss, -no-strict-syntax Disable strict syntax check on templates
-tl list all available templates
FILTERING:
-a, -author string[] templates to run based on authors (comma-separated, file)
-tags string[] templates to run based on tags (comma-separated, file)
-etags, -exclude-tags string[] templates to exclude based on tags (comma-separated, file)
-itags, -include-tags string[] tags to be executed even if they are excluded either by default or configuration
-id, -template-id string[] templates to run based on template ids (comma-separated, file)
-eid, -exclude-id string[] templates to exclude based on template ids (comma-separated, file)
-it, -include-templates string[] templates to be executed even if they are excluded either by default or configuration
-et, -exclude-templates string[] template or template directory to exclude (comma-separated, file)
-em, -exclude-matchers string[] template matchers to exclude in result
-s, -severity value[] templates to run based on severity. Possible values: info, low, medium, high, critical, unknown
-es, -exclude-severity value[] templates to exclude based on severity. Possible values: info, low, medium, high, critical, unknown
-pt, -type value[] templates to run based on protocol type. Possible values: dns, file, http, headless, network, workflow, ssl, websocket, whois
-ept, -exclude-type value[] templates to exclude based on protocol type. Possible values: dns, file, http, headless, network, workflow, ssl, websocket, whois
OUTPUT:
-o, -output string output file to write found issues/vulnerabilities
-sresp, -store-resp store all request/response passed through nuclei to output directory
-srd, -store-resp-dir string store all request/response passed through nuclei to custom directory (default "output")
-silent display findings only
-nc, -no-color disable output content coloring (ANSI escape codes)
-json write output in JSONL(ines) format
-irr, -include-rr include request/response pairs in the JSONL output (for findings only)
-nm, -no-meta disable printing result metadata in cli output
-nts, -no-timestamp disable printing timestamp in cli output
-rdb, -report-db string nuclei reporting database (always use this to persist report data)
-ms, -matcher-status display match failure status
-me, -markdown-export string directory to export results in markdown format
-se, -sarif-export string file to export results in SARIF format
CONFIGURATIONS:
-config string path to the nuclei configuration file
-fr, -follow-redirects enable following redirects for http templates
-mr, -max-redirects int max number of redirects to follow for http templates (default 10)
-dr, -disable-redirects disable redirects for http templates
-rc, -report-config string nuclei reporting module configuration file
-H, -header string[] custom header/cookie to include in all http request in header:value format (cli, file)
-V, -var value custom vars in key=value format
-r, -resolvers string file containing resolver list for nuclei
-sr, -system-resolvers use system DNS resolving as error fallback
-passive enable passive HTTP response processing mode
-ev, -env-vars enable environment variables to be used in template
-cc, -client-cert string client certificate file (PEM-encoded) used for authenticating against scanned hosts
-ck, -client-key string client key file (PEM-encoded) used for authenticating against scanned hosts
-ca, -client-ca string client certificate authority file (PEM-encoded) used for authenticating against scanned hosts
-sml, -show-match-line show match lines for file templates, works with extractors only
-ztls use ztls library with autofallback to standard one for tls13
-sni string tls sni hostname to use (default: input domain name)
INTERACTSH:
-iserver, -interactsh-server string interactsh server url for self-hosted instance (default: oast.pro,oast.live,oast.site,oast.online,oast.fun,oast.me)
-itoken, -interactsh-token string authentication token for self-hosted interactsh server
-interactions-cache-size int number of requests to keep in the interactions cache (default 5000)
-interactions-eviction int number of seconds to wait before evicting requests from cache (default 60)
-interactions-poll-duration int number of seconds to wait before each interaction poll request (default 5)
-interactions-cooldown-period int extra time for interaction polling before exiting (default 5)
-ni, -no-interactsh disable interactsh server for OAST testing, exclude OAST based templates
RATE-LIMIT:
-rl, -rate-limit int maximum number of requests to send per second (default 150)
-rlm, -rate-limit-minute int maximum number of requests to send per minute
-bs, -bulk-size int maximum number of hosts to be analyzed in parallel per template (default 25)
-c, -concurrency int maximum number of templates to be executed in parallel (default 25)
-hbs, -headless-bulk-size int maximum number of headless hosts to be analyzed in parallel per template (default 10)
-headc, -headless-concurrency int maximum number of headless templates to be executed in parallel (default 10)
OPTIMIZATIONS:
-timeout int time to wait in seconds before timeout (default 5)
-retries int number of times to retry a failed request (default 1)
-ldp, -leave-default-ports leave default HTTP/HTTPS ports (eg. host:80,host:443
-mhe, -max-host-error int max errors for a host before skipping from scan (default 30)
-project use a project folder to avoid sending same request multiple times
-project-path string set a specific project path
-spm, -stop-at-first-path stop processing HTTP requests after the first match (may break template/workflow logic)
-stream stream mode - start elaborating without sorting the input
-irt, -input-read-timeout duration timeout on input read (default 3m0s)
-no-stdin Disable Stdin processing
HEADLESS:
-headless enable templates that require headless browser support (root user on linux will disable sandbox)
-page-timeout int seconds to wait for each page in headless mode (default 20)
-sb, -show-browser show the browser on the screen when running templates with headless mode
-sc, -system-chrome Use local installed chrome browser instead of nuclei installed
DEBUG:
-debug show all requests and responses
-dreq, -debug-req show all sent requests
-dresp, -debug-resp show all received responses
-p, -proxy string[] list of http/socks5 proxy to use (comma separated or file input)
-pi, -proxy-internal proxy all internal requests
-tlog, -trace-log string file to write sent requests trace log
-elog, -error-log string file to write sent requests error log
-version show nuclei version
-hm, -hang-monitor enable nuclei hang monitoring
-v, -verbose show verbose output
-vv display templates loaded for scan
-ep, -enable-pprof enable pprof debugging server
-tv, -templates-version shows the version of the installed nuclei-templates
-hc, -health-check run diagnostic check up
UPDATE:
-update update nuclei engine to the latest released version
-ut, -update-templates update nuclei-templates to latest released version
-ud, -update-directory string overwrite the default directory to install nuclei-templates
-duc, -disable-update-check disable automatic nuclei/templates update check
STATISTICS:
-stats display statistics about the running scan
-sj, -stats-json write statistics data to an output file in JSONL(ines) format
-si, -stats-interval int number of seconds to wait between showing a statistics update (default 5)
-m, -metrics expose nuclei metrics on a port
-mp, -metrics-port int port to expose nuclei metrics on (default 9092)运行原子核
使用社区策划的细胞核模板扫描目标域。
nuclei -u https://example.com使用社区策划的核模板扫描目标 URL。
nuclei -list urls.txt示例:
urls.txt
http://example.com
http://app.example.com
http://test.example.com
http://uat.example.com可以在此处找到运行原子核的更多详细示例。
对于安全工程师
Nuclei提供了大量的功能,有助于安全工程师在组织中自定义工作流程。借助各种扫描功能(如 DNS、HTTP、TCP),安全工程师可以使用 Nuclei 轻松创建自定义检查套件。
- 支持的多种协议:TCP,DNS,HTTP,文件等
- 通过工作流和动态请求实现复杂的漏洞步骤。
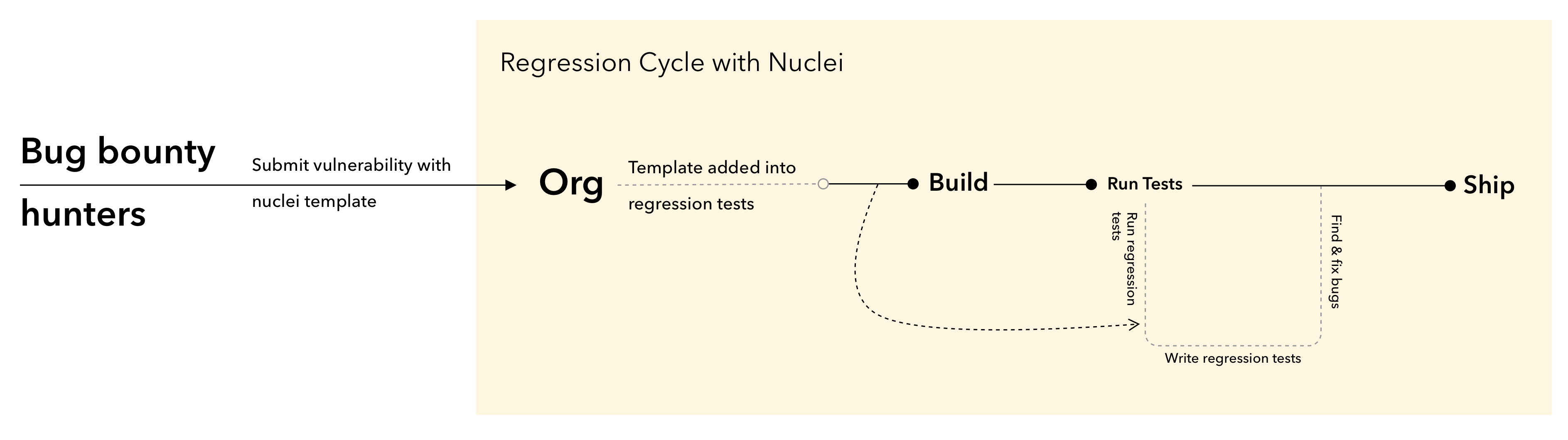
- 易于集成到 CI/CD 中,旨在轻松集成到回归循环中,以主动检查漏洞的修复和重新出现。
|
对于漏洞赏金猎人: Nuclei允许你使用自己的检查套件自定义测试方法,并轻松运行你的错误赏金程序。此外,Nuclei可以很容易地集成到任何连续扫描工作流程中。
请查看我们的其他开源项目,这些项目可能适合你的错误赏金工作流程:github.com/projectdiscovery,我们还在Chaos托管DNS数据的每日刷新。 |
|
对于渗透测试人员: Nuclei 通过增强手动、重复的流程,极大地改善了你进行安全评估的方式。咨询公司已经在使用Nuclei转换他们的手动评估步骤,它允许他们以自动方式在数千台主机上运行他们的自定义评估方法。 渗透测试人员可以充分利用我们的公共模板和自定义功能,以加快他们的评估过程,特别是回归周期,你可以在其中轻松验证修复。 |
对于开发人员和组织
Nuclei的构建考虑了简单性,由数百名安全研究人员支持社区模板,它允许你使用主机上的连续Nuclei扫描随时了解最新的安全威胁。它旨在轻松集成到回归测试周期中,以验证修复并消除将来发生的漏洞。
- CI/CD:工程师们已经在他们的CI/CD管道中使用Nuclei,它允许他们使用自定义模板持续监控其过渡和生产环境。
- 连续回归周期:借助Nuclei,你可以在每个新识别的漏洞上创建自定义模板,并将其放入Nuclei引擎以在连续回归周期中消除。
我们有一个围绕这个问题的讨论线程,已经有一些漏洞赏金程序激励黑客在每次提交时编写核心模板,这有助于他们消除所有资产中的漏洞,并消除未来在制作中重新出现的风险。如果你有兴趣在你的组织中实施它,请随时与我们联系。我们将非常乐意在入门过程中为你提供帮助,或者你也可以发布到讨论线程以获取任何帮助。
资源
- 用PinkDraconian(Robbe Van Roey)寻找Nuclei的bug by @PinkDraconian
- Nuclei: Pack a Punch with Vulnerabilit Scanning by Bishopfox
- 快速提供的 WAF 功效框架
- 按@TristanKalos扫描 CI/CD 管道中具有 Nuclei 的实时 Web 应用程序
- 使用 Nuclei 进行社区支持的扫描
- 释放原子核 - 快速写入复杂的漏洞利用
- 原子核 - 模糊所有的东西
- 用于自动化 OOB 测试的 Nuclei + Interactsh 集成
- 通过@dwisiswant0将原子核工作流程武器化为Pwn所有事物
- 如何使用原子核连续扫描?由 @dwisiswant0
- 使用自动化!!!进行黑客攻击作者:@DhiyaneshGeek
捐赠
感谢所有出色的社区贡献者发送PR。另请查看以下可能适合你工作流程的类似开源项目:
FFuF, Qsfuzz, Inception, Snallygaster, Gofingerprint, Sn1per, Google tsunami, Jaeles, ChopChop
许可证
Nuclei在MIT许可证下分发